Solana Account Dusting & Address Poisoning
Executive Summary
Solana’s fast, low-cost architecture has enabled widespread adoption—but it has also introduced a fertile environment for a new category of transaction-level spam and deception. This report investigates two emerging forms of abuse that exploit the predictability of user behavior and interface design: domain-based dusting and surgical address poisoning.
Domain-based dusting involves spamming wallets with uneconomical micro-transactions from vanity-named addresses (e.g., flip.gg, casino.sol). These are designed to grab user attention in wallet history views and redirect them to off-chain scams, gambling sites, or phishing pages.
Address poisoning is a more covert threat, where attackers inject lookalike addresses into wallet histories with the intent of being mistaken for a legitimate recipient. This method has already led to multimillion-dollar losses—and it targets even experienced users by exploiting UI design patterns and cognitive shortcuts.
In this paper, we’ll walk you through how to understand these threats, how we built tools to detect and prevent them, and what tradeoffs we considered while designing each system.
Domain-Based Dusting
Identifying Domain-Based Dusting
This analysis aims to detect malicious actors using domain-based dusting attacks on Solana. These attackers typically send tiny, uneconomical amounts of SOL to thousands of wallets, often using vanity domains (e.g., flip.gg, casino.sol) to bait users into engagement—whether for scams, gambling sites, or phishing attempts.
1. Establishing the 7-Day Behavior Window
To evaluate whether a transaction is part of a domain-based dusting pattern, we analyze the behavior of the sender wallet in the 7 days prior to that transaction.
We extract all SOL transfers made by that wallet during this period and focus on transactions where all transferred amounts are less than 0.000005 SOL—the minimum gas fee required to send a transaction—and where native SOL is the only token sent. Sending less than this amount means each recipient receives less value than it costs to send, which typically suggests the transfers are not economically motivated.
For the wallet, we calculate:
The number of unique wallets they sent less than 0.000005 SOL to
The total number of transactions and transfer events
The total amount of SOL transferred
The estimated minimum gas cost (assuming 0.000005 SOL per transaction)
2. Checking for Domain Registration
Next, we check whether the sender wallet has registered a domain through either of the following platforms:
The Solana Name Service (SNS)
The AllDomains registry
These platforms provide vanity names (e.g., flip.gg, something.sol) that are often used by spam bots to appear more legitimate or recognizable in transaction history, increasing the likelihood of user engagement.
3. Flagging Domain-Based Dusting
A transaction is classified as part of a domain-based dusting campaign if, in the 7 days leading up to it, the sender wallet with a registered domain Has spent at least 2× more on gas than the total SOL value transferred (i.e., percent_of_gas < 50%).
This thresholds isolate wallets exhibiting behavior that is:
Economically irrational
Visibly branded
Mass-scale and unsolicited
Such transactions degrade the user experience, clutter wallet histories, and may expose users to off-chain scams or phishing attempts.
On Multisend Behavior
We also considered using multisend behavior (i.e., multiple transfer events per transaction) as an additional detection signal. However, we found it to be redundant—nearly all domain-based dusting bots already use multisend as a cost-saving technique. Including it did not meaningfully improve detection accuracy, so we excluded it from the final classification logic.
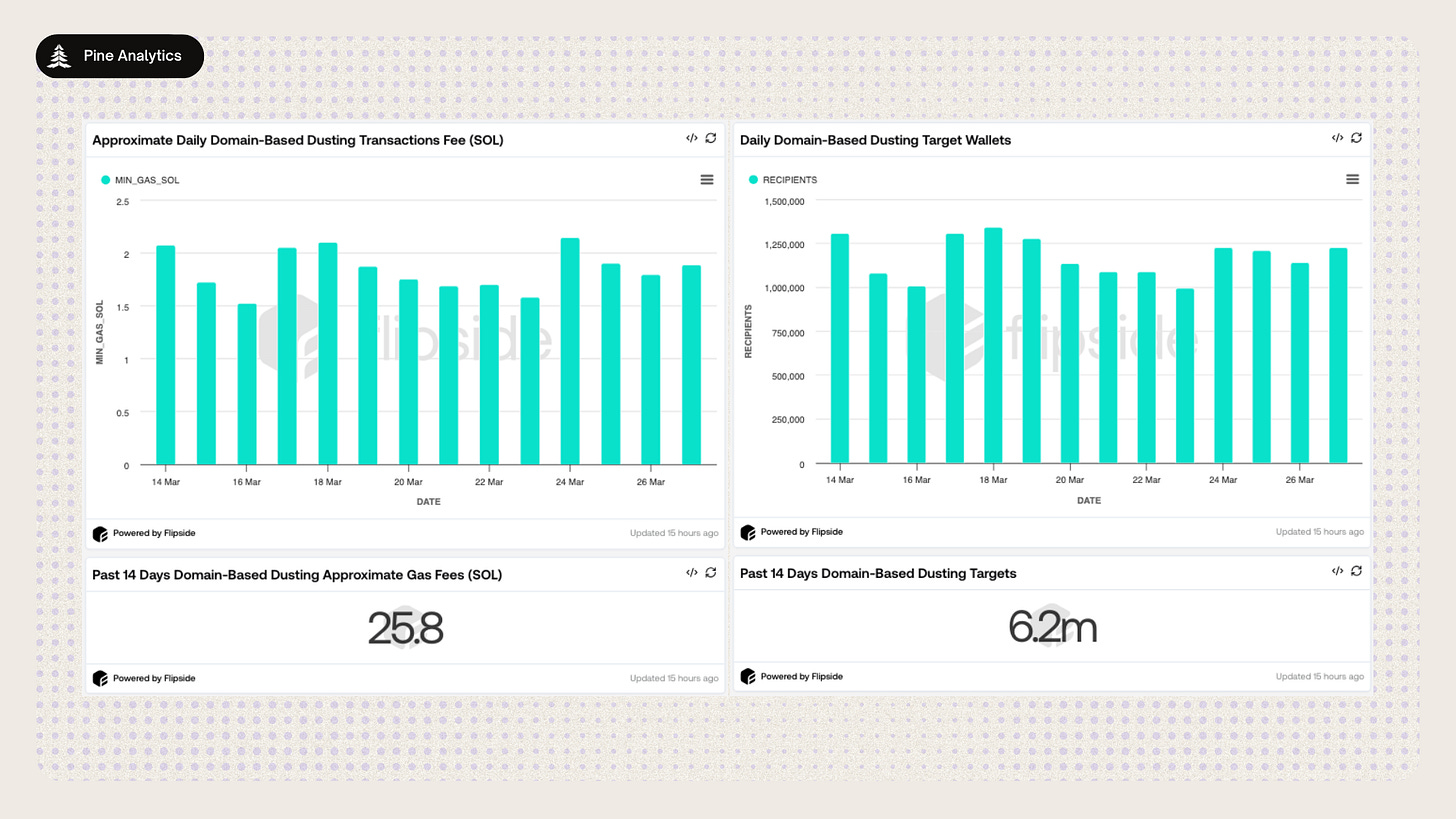
The Scale of Domain-Based Dusting
Over the past 14 days, we identified 40 active wallets engaging in domain-based dusting campaigns on Solana. Together, these wallets have targeted an estimated 6.2 million unique addresses, with daily dusting activity ranging between 1 million and 1.25 million wallets per day.
In total, these wallets executed 5.2 million dusting transactions, containing over 84 million individual SOL transfers—almost all below the minimum viable transfer value. And yet, the total cost remains remarkably low given the massive reach:
1.5 to 2 SOL per day spent on gas
0.01 to 0.05 SOL per day spent on the dust itself
26.1 SOL total across 14 days of activity
When breaking down sender behavior by reach:
4 wallets have dusted over 1 million addresses each
25 wallets have targeted between 1,000 and 100,000 addresses
And by spend:
6 wallets have spent more than 1 SOL
23 wallets have spent between 0.01 and 0.1 SOL
Given the level of visibility these campaigns achieve—cluttering millions of wallets and even prompting articles like this—the cost is shockingly efficient. For less than the price of a single high-profile tweet or ad campaign, these actors are reaching the entire Solana network with domain-branded messages embedded directly in wallet histories.
Domain-Based Dusting Actors
While many domain-linked wallets engage in dusting on Solana, the following represent some of the most active culprits over the past two weeks. Each has spent significant SOL on gas fees to send uneconomical micro-transactions to thousands of wallets—typically as a form of unsolicited promotion.
This list is by no means exhaustive, but it highlights a few of the most aggressive actors currently polluting transaction histories with low-value spam. Here's a closer look at what they're doing—and what they appear to be promoting.
Flip.gg: A Solana-based gambling platform using lootbox mechanics. Its wallets, registered under multiple vanity domains, sent uneconomical dust to millions of addresses, spending over 18 SOL in the past two weeks—far exceeding the value transferred.
OdinBot.io: A copy-trading platform that repeatedly dusted thousands of wallets using long vanity domains like "odinbot-io⚡fastest-copy-trading.sol." Its wallets spent just over 3 SOL on gas for these unsolicited micro-transactions.
Crashout.fun: A gambling game built around crash-style mechanics. Using emoji-laden vanity domains, Crashout.fun dusted users to drive traffic. Their wallets spent ~4 SOL over two weeks despite transferring negligible value.
WalletX.gg: A wallet analysis tool promoting via promo-style addresses such as "👉walletx-gg👈alpha-wallets-scraper.sol." It executed widespread dusting activity while spending just 0.25 SOL, suggesting a high ROI for this form of unsolicited promotion.
Surgical Address Poisoning Attacks
Identifying Address Poisoning
Surgical address poisoning is a subtle and predatory attack vectors in modern crypto. Unlike traditional phishing, which often depends on user error, this technique exploits a completely different vulnerability: the predictable habits of even cautious users. Specifically, it targets the common behavior of copying and pasting recently used wallet addresses from one’s transaction history.
What makes this attack especially dangerous is its elegance:
It requires no permissions
It involves no interaction with the attacker
And it can succeed even if the user double-checks the address
This isn’t an attack on recklessness — it’s an attack on routine. Even users with strong operational security, who avoid airdrops and verify contracts, can fall victim simply by reusing a familiar-looking address. Once injected into the transaction history, a malicious address with carefully crafted visual similarity can quietly redirect funds.
A Real-World Loss: $2.9M Stolen via Address Poisoning
In November 2024, a Solana user lost $2.91 million after mistakenly copying a spoofed centralized exchange (CEX) deposit address from their wallet transaction history. Despite appearing nearly identical to the legitimate address, it was a malicious vanity address planted by an attacker—demonstrating just how effective this attack vector can be.
Victim Address:
5LbwC1ewY3Sca7T8CwzX9wsjvwMAHbdRo6SCQL8j7EWcSpoofed Address:
4yfuQCL4fnNfSbBgqFcPTFn5GGZABDaEFQLhGpwjizcYCorrect Address:
4yfu48qwim7hGzD3Nphzd2A6ThydzysfKi4wBPFSgnhY
The addresses differ by just a few characters—enough to fool even attentive users, especially when relying on wallet UIs that display shortened versions.
“This isn’t an attack on recklessness—it’s an attack on routine.”
This incident, viewed over 120,000 times on Twitter, catalyzed urgent community discussion and underlines the importance of detection tooling like the system described in this report.
Filtering for Candidate Transactions
To detect poisoning attempts with precision — while minimizing false positives — we begin with a focused filter to isolate only those transactions that exhibit the structural and behavioral signature of surgical address poisoning.
Transfer size is small (often < 0.5 SOL, typically below gas cost)
Occurs shortly after a high-value legitimate transfer
Sent to the same sender as the legitimate transfer
Sender address visually resembles the legitimate recipient
Sender wallet is recently created (often within 24 hours)
This tight filter ensures that we’re not simply flagging unusual behavior — we’re isolating transactions that structurally and behaviorally match known poisoning tactics.
Why Each Signal Matters
Visual Similarity
At the core of the attack is visual deception. Poisoning relies on vanity-generated addresses that resemble legitimate ones — particularly at the beginning and end of the address, where users typically focus when verifying.
We score matches based on how many characters align visually at the front and back of the address. These patterns correspond to statistically improbable collisions:
Matching 2 characters at the start and 2 at the end has a ~1 in 11 million chance of occurring randomly
Matching 3 characters at the start and 3 at the end has a ~1 in 38 billion chance
The higher the number of matching characters, the less likely it’s a coincidence — and the more likely it’s an intentional attempt to deceive.
Timing Proximity
Timing plays a critical role in effectiveness. Poisoning is most successful when the attacker sends the dust immediately after a high-value transaction. This places the spoofed transaction directly adjacent to the legitimate one in the wallet UI — increasing the chance that the user copies the wrong address. For this reason, we weight transactions more heavily if they occur within minutes of a large transfer.
Wallet Age
Attackers often generate fresh wallets using vanity tools, then deploy them immediately to dust targets. These wallets have no history or identity — just a forged appearance. We treat wallets created within 24 hours of the poisoning attempt as high risk, since their short lifespan strongly suggests a disposable, automated attack source.
Amount Constraints
Most poisoning attempts aim to be invisible — sending dust so small it flies under wallet filters and seems benign. These transactions often transfer less than the cost of gas, making them effectively free for the attacker.
However, we also account for high-effort attacks. Generating a high-similarity vanity address (e.g., 3+3) can cost up to $30 in compute time. In these cases, it's plausible an attacker would send a larger amount — possibly to impersonate a refund or to blend in with legitimate transaction patterns.
To account for this, we penalize transactions only when the amount exceeds what's reasonable for its similarity level. This allows us to:
Flag low-effort spam with high confidence
Avoid false positives from small, legitimate transfers
Detect escalated attacks where the deception is sophisticated — and the stakes are higher
Mathematical Rationale
The strength of this detection system lies in the predictable structure of vanity address generation and the mathematically quantifiable rarity of visual similarities. Unlike probabilistic spam or phishing filters, this approach leverages fixed entropy distributions (from Solana’s Base58 address format) and real-world compute cost models to identify surgical poisoning with high confidence.
Address Match Probabilities
Solana addresses are 44-character Base58 strings. The probability of two randomly generated addresses matching on the same characters is extremely low — and decreases exponentially with each additional character:
1 character match: 1 in 58
2 characters: 1 in 3,364
3 characters: 1 in 195,112
4 characters: 1 in 11.3 million
5 characters: 1 in 656 million
6 characters: 1 in 38 billion
7+ characters: functionally impossible without brute force
We calculate similarity based on the number of matching characters at the start and end of the address, such as “match first 2 and last 2 characters.” These combined match patterns serve as the foundation for our visual risk scoring system.
Given these odds, high-similarity, low-value transactions are statistically implausible without deliberate attacker intent. It can be extremely valuable to automatically discard matches that involve 4 or more matching characters on both sides — which are both vanishingly rare and visually dangerous. The recent $2.9M poisoning attack, for example, involved a 5-character overlap.
The only realistic edge cases — where a transaction may appear risky but not be malicious — occur at the lower similarity levels:
Matching 1 character at the start and 1 at the end (score 1): ~1 in 3,364
Matching 1 character on one side and 2 on the other (score 2): ~1 in 195,112
Alone, these patterns aren’t suspicious in large datasets. But when they coincide with other attacker behaviors, they become meaningful signals.
Handling Edge Case Matches (Low Similarity)
To safely detect low-similarity poisoning attempts without flagging legitimate transactions, we apply a context-aware scoring system that adapts based on surrounding signals:
If a suspicious transaction occurs within five minutes of a large, legitimate transfer, we apply a timing-based score boost, reflecting likely manipulation of wallet history ordering.
If the sending wallet is less than 24 hours old, we apply a wallet age bonus, as freshly generated vanity addresses are common in these attacks.
If the transfer amount exceeds the dust threshold for its match class, we apply a penalty, reflecting the decreased likelihood of deception at larger values.
This layered heuristic distinguishes natural coincidences (e.g., small transfers from old wallets) from intentional low-effort deception — and escalates only when multiple risk factors align.
Result: Precision Without Overreach
With this system in place, we:
Flag edge-case matches only when reinforced by other high-signal indicators
Minimize false positives, even in large, high-throughput environments
Preserve full auditability, providing clear insight into every score assigned
In rare cases where a benign system intentionally generates high-similarity addresses — such as for branding or user experience — those wallets can be safely whitelisted to avoid misclassification.
Detection Tooling and Implementation
To move from theory to action, we developed tools capable of identifying both domain-based dusting and address poisoning attacks. These tools are designed for wallet providers, explorers, and researchers who need to flag or filter suspicious transactions at scale. All of them rely on Flipside and/or Helius as the underlying data provider.
Dusting Activity Dashboard
https://flipsidecrypto.xyz/pine/domain-based-dusting-metrics-0v65qW
A Flipside-hosted dashboard that:
Tracks the daily activity of identified domain-based dusting wallets over the past 14 days.
Surfaces vanity domain wallers tied to active spam campaigns
Shows gas usage, dust volume, and total wallets targeted of all campains over ths past 2 weeks
Daily Dusting Query
https://flipsidecrypto.xyz/studio/queries/9fe973d5-ea06-493a-b5a5-3b92f7880e7c
A Flipside-hosted query that tracks daily metrics for each identified dusting wallet, based on activity in the 7 days prior to each row’s creation date. Updated daily, it captures a rolling window of dusting behavior.
Includes:
The number of wallets that received dust from the duster in the 7 days prior
The volume of SOL sent to wallets that received dust in the 7 days prior
The minimum amount of SOL the duster could have spent on gas fees in the 7 days prior
The number of SOL dusting events in the 7 days prior
The number of SOL dusting transactions in the 7 days prior
Use case: It can also be used as a live list of currently active dusting wallets — making it easy to plug into other Flipside queries or external codebases for real-time detection, monitoring, or response automation.
Domain-Based Dusting Transaction Classifier (Python)
https://github.com/jms1192/dust-tx_checker
A Python script that:
Accepts a list of Solana transaction IDs (
tx_ids) and a Helius API key as inputFetches decoded transfer data from the Helius API
Cross-references sending wallets against Flipside’s live list of domain-based dusting addresses
Classifies each transaction as
DUSTINGorclean
Returns: A dictionary mapping each tx_id to a Boolean dusting verdict
Use case: Lightweight forensic tool for security analysts, bot integrations, or Solana infrastructure teams looking to flag dusting activity in real time.
Address Poisoning Risk Scorer (Python Script)
https://github.com/jms1192/Poisoning_checker
Accepts a list of tx_ids
Calculates risk based on:
Address similarity, such as front and back address character matches (e.g., 3-character prefix and 3-character suffix match)
transaction timing (proximity to recent inbound funds)
wallet age (time since first funding)
transfer amount (adjusted for spoofing thresholds)
Returns: a normalized risk score (0–100) and risk label (Clean, Low, Medium-Low, Medium, High)
Uses: Flipside Crypto as the backend query engine — subject to ~15-minute data lag due to ingestion delay
Use case: scoring batches of Solana transactions for address poisoning attempts.
Final Thoughts
After diving deep into domain-based dusting and address poisoning, one thing is obvious: the most common and harmful variants of these attacks can be caught with simple, scalable logic — and nearly eliminated at the wallet level.
For dusting, nearly all low-value vanity sends can be filtered out without risk. Forcing attackers to send larger amounts to get through filters would make the entire campaign uneconomical almost immediately.
For address poisoning, it’s just math. Wallets that share more than 4 matching characters (front and back) with a recent address are statistically impossible to occur naturally — those can be filtered outright. For lower-similarity cases, combining with factors like suspicious timing or fresh wallet creation gives more than enough signal to confidently flag or hide the transaction.
These aren't protocol-level flaws — they're interface gaps. And fixing them doesn’t require deep ML or new standards. Just some well-placed filters.